As usual when you see a strange mail appear in your mail box you should be hearing little alarm bells.
This one even came from an obviously suspicious source in this case "MISSY Clayton
The mail title "Fwd: Scan from a Xerox W. Pro #348663"
And the content .. dear oh dear ... it's a HTM file
Strange, in all my 30 years working on printers I've not worked on an MFP that scans documents and converts them to HTML !
The HTM (when viewed as a text file shows)
(I've done it as a JPEG, if I paste the code in it executes... doh)
Now I'm not a Java or scripting chappie, I understand the header is announcing it's HTML 4 format so the bit that interests me is the script below, it's obviously there to do something ?
I can see it will put up a "Loading .... Please wait" message
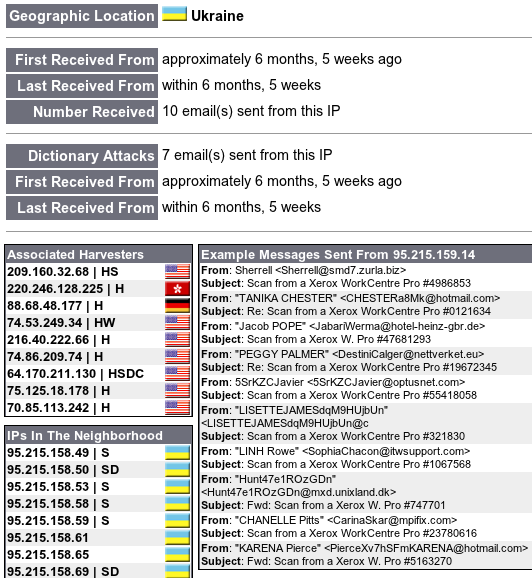
IP address given is 95.215.159.14 not surprising that this comes up as an unknown IP address when you look up the domain.
Looking up hotel-heinz-gbr.de does yield a result which appears to be in a hosting service just here.....
My spider senses tell me this emails not legitimate ????
Honeypot further warns on some of the mail tags used previously but not an exhaustive list. Hmm the mail titles look familiar.
It would be interesting if anyone knew what the code did, If it's something nasty I might need to edit this post and delete some code so no one else can use it?
I suspect it's running a keylogger or virus or just something nasty ?